
祭出神器Fiddler,安装新浪邮箱到模拟器。抓包得
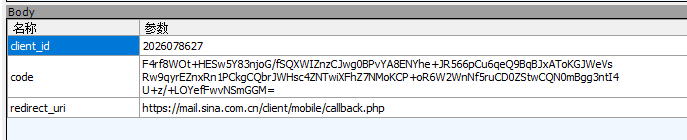
分析可得code明细加密。
然后我们把APK拉入jadx看看反汇编代码如何
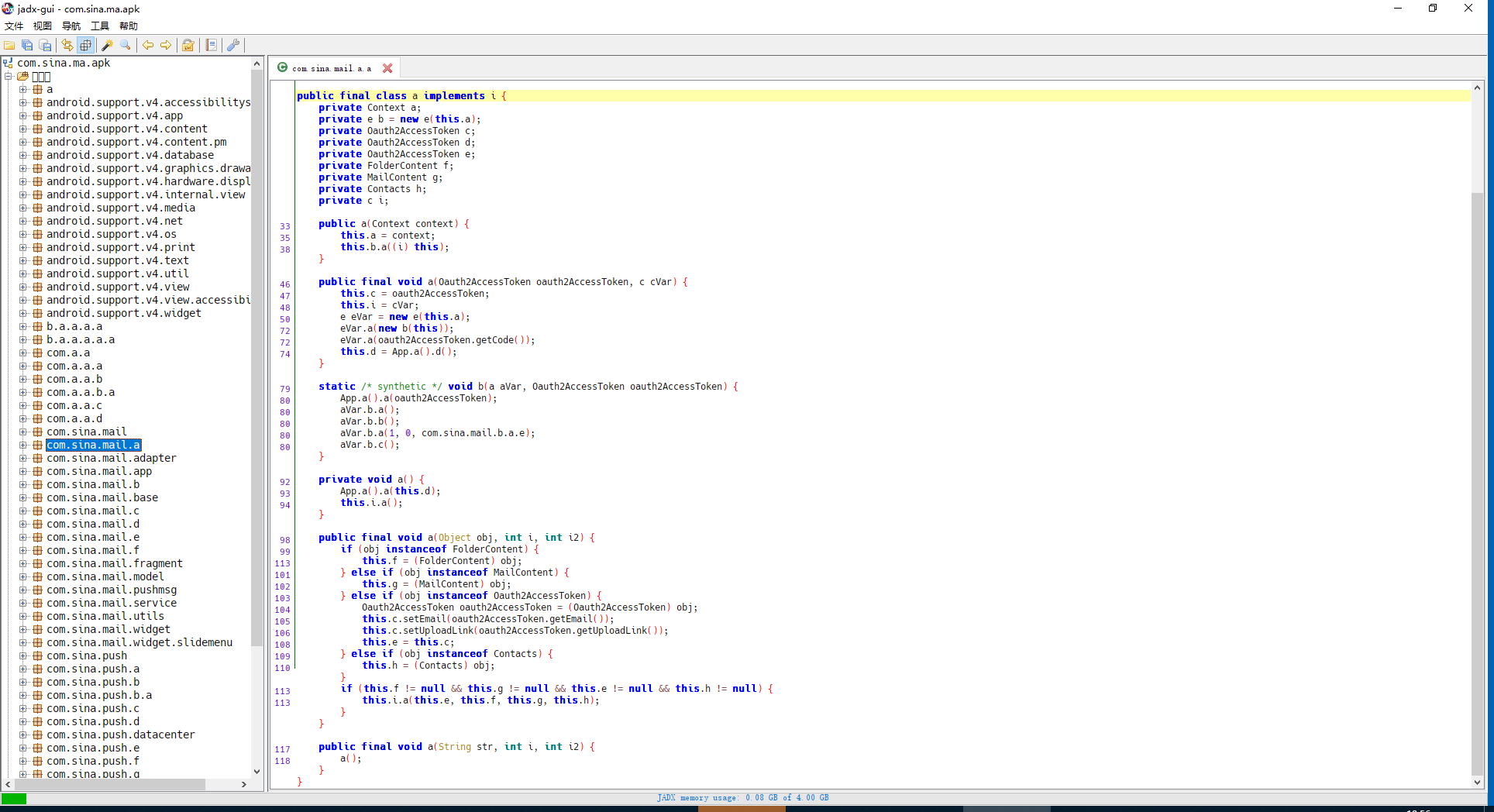
虽然混淆过。但是还是不错得。
分别查找下client_id,code,redirect_uri
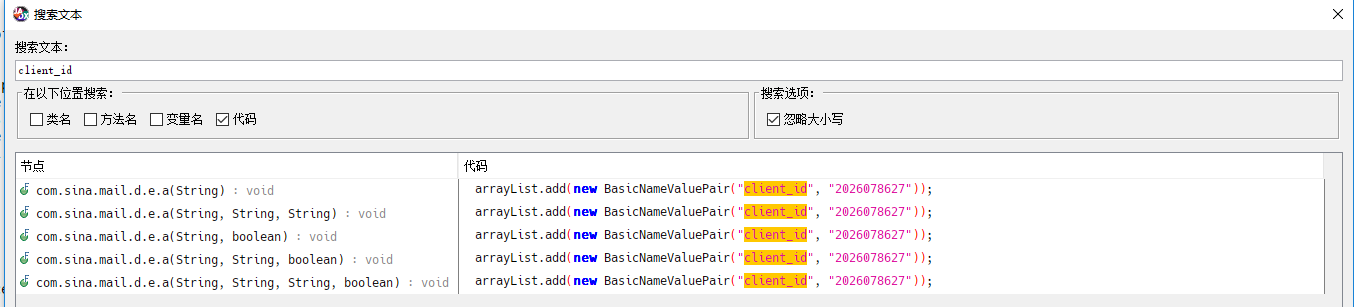
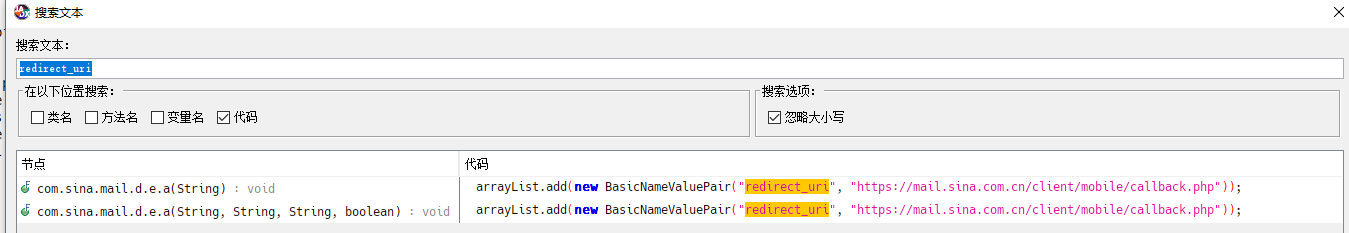
之后进入com.sina.mail.d.e类看看
public final void a(String str) {
List arrayList = new ArrayList();
arrayList.add(new BasicNameValuePair("client_id", "2026078627"));
arrayList.add(new BasicNameValuePair(Columns.CODE, str));
arrayList.add(new BasicNameValuePair("redirect_uri", "https://mail.sina.com.cn/client/mobile/callback.php"));
this.a.a("/1/sauth", Oauth2AccessToken.class, arrayList);
}
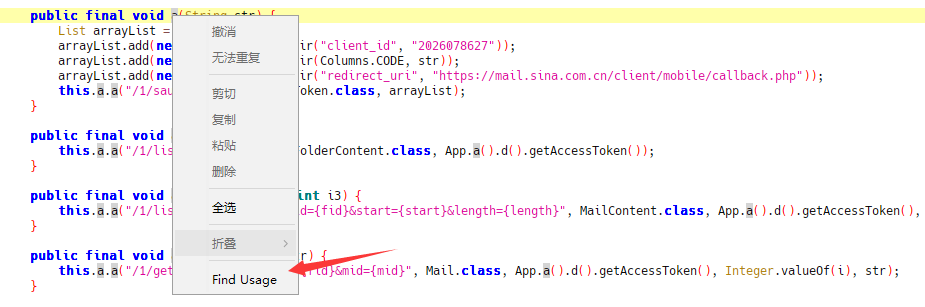
对着函数a 邮件FindUsage查看引用整个函数得有什么地方
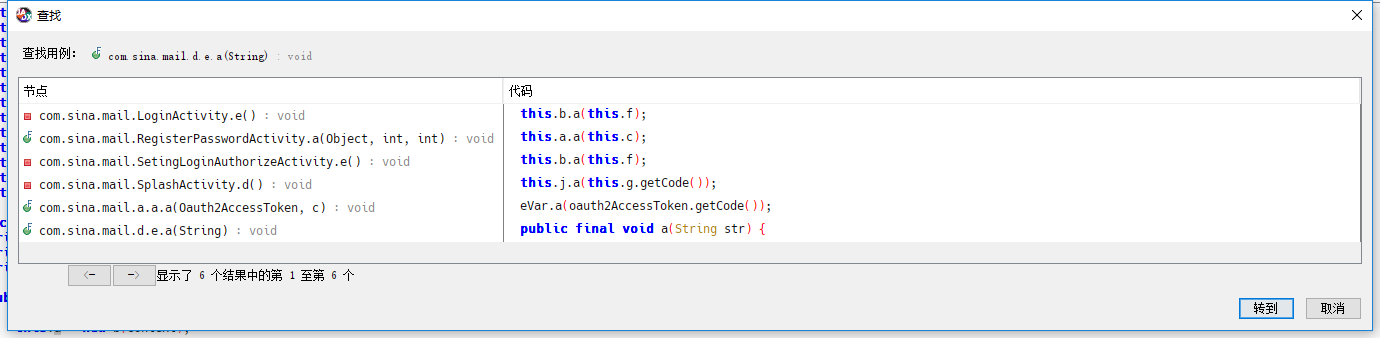
需要引用我们注意得是第一个。因为LoginActivity就是登陆动作
private void e() {
try {
String editable = this.c.getText().toString();
String editable2 = this.e.getText().toString();
if (bh.a(editable)) {
bh.a((Context) this, (int) C0000R.string.login_please_input_account);
} else if (bh.a(editable2)) {
bh.a((Context) this, (int) C0000R.string.login_please_input_password);
} else {
this.f = k.a(editable, editable2);
this.b.a(this.f);
}
} catch (Exception e) {
}
}
因为我们知道从CODE是从这里传回来得。this.b.a(this.f);就是调用com.sina.mail.d.e.a(str)
所以综合,k.a(editable, editable2)这个就是关键得函数
右键FindUsage
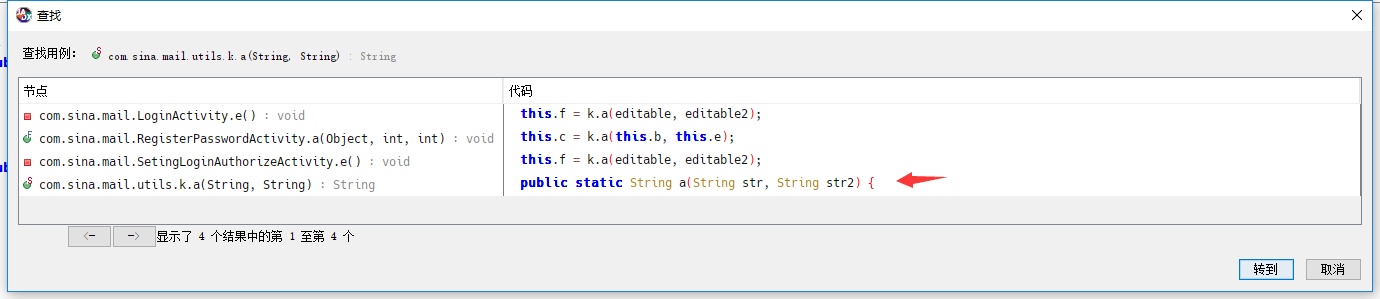
第四个就是静态方法。双击跟进
package com.sina.mail.utils;
public final class k {
public static String a(String str, String str2) {
return as.a(as.a("MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCr6uxto9ld75P2oiV/DD51yr080zz7JMY4W+s2GE6gKtGOxwdFju+s4HNRQKPCh70Vt7tkovNIVt0/3Zyl9r7fgGDJGbssur1xJB1Xi/9zNY0mk5StBloaZbNbW+7ZbQh9AE1lY8LsqWqvn7PLZKMTWXFc0nDoCU9IERZDM9cizQIDAQAB"), str + ":" + str2);
}
}
开始出现数据了。真相就在眼前。继续查看哪里调用了as.a然后找出下面得一个as类
package com.sina.mail.utils;
import a.a;
import a.b;
import java.io.ByteArrayInputStream;
import java.io.ByteArrayOutputStream;
import java.security.InvalidKeyException;
import java.security.KeyFactory;
import java.security.NoSuchAlgorithmException;
import java.security.PublicKey;
import java.security.spec.X509EncodedKeySpec;
import javax.crypto.BadPaddingException;
import javax.crypto.Cipher;
import javax.crypto.IllegalBlockSizeException;
import javax.crypto.NoSuchPaddingException;
public final class as {
private static Cipher a;
static {
try {
a = Cipher.getInstance("RSA/ECB/PKCS1Padding");
} catch (NoSuchAlgorithmException e) {
e.printStackTrace();
} catch (NoSuchPaddingException e2) {
e2.printStackTrace();
}
}
public static PublicKey a(String str) {
a aVar = new a();
byte[] bArr = new byte[str.length()];
str.getBytes(0, str.length(), bArr, 0);
ByteArrayInputStream byteArrayInputStream = new ByteArrayInputStream(bArr);
ByteArrayOutputStream byteArrayOutputStream = new ByteArrayOutputStream();
aVar.a(byteArrayInputStream, byteArrayOutputStream);
return KeyFactory.getInstance("RSA").generatePublic(new X509EncodedKeySpec(byteArrayOutputStream.toByteArray()));
}
public static String a(PublicKey publicKey, String str) {
try {
a.init(1, publicKey);
return new b().a(a.doFinal(str.getBytes()));
} catch (InvalidKeyException e) {
e.printStackTrace();
} catch (IllegalBlockSizeException e2) {
e2.printStackTrace();
} catch (BadPaddingException e3) {
e3.printStackTrace();
}
return null;
}
}
现在数据有了,类也找到了。
得到得算法下:
填充方式:PKCS1_PADDING 字符集:UTF8编码
公钥为:
-----BEGIN PUBLIC KEY----- MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCr6uxto9ld75P2oiV/DD51yr08 0zz7JMY4W+s2GE6gKtGOxwdFju+s4HNRQKPCh70Vt7tkovNIVt0/3Zyl9r7fgGDJ Gbssur1xJB1Xi/9zNY0mk5StBloaZbNbW+7ZbQh9AE1lY8LsqWqvn7PLZKMTWXFc 0nDoCU9IERZDM9cizQIDAQAB -----END PUBLIC KEY-----
加密数据:111111@sina.cn:111111
格式:邮箱:密码
因为没有私钥不能解密。
后面我不放心通过验证算法加密提交过也证明是对得。