使用模拟器运行软件后,观察得出下面抓包数据
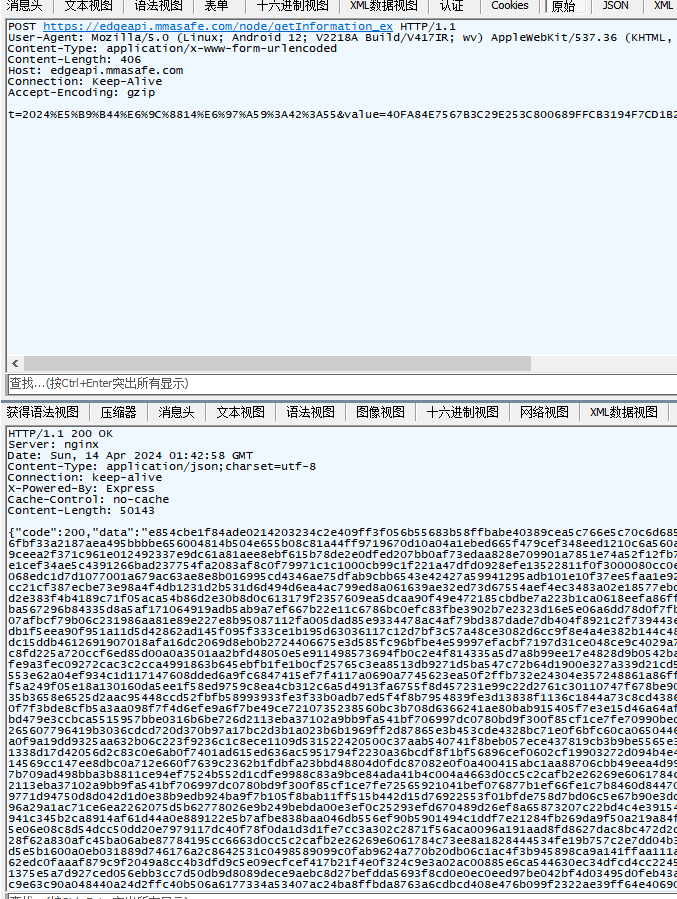
算法助手里也出现相关数据
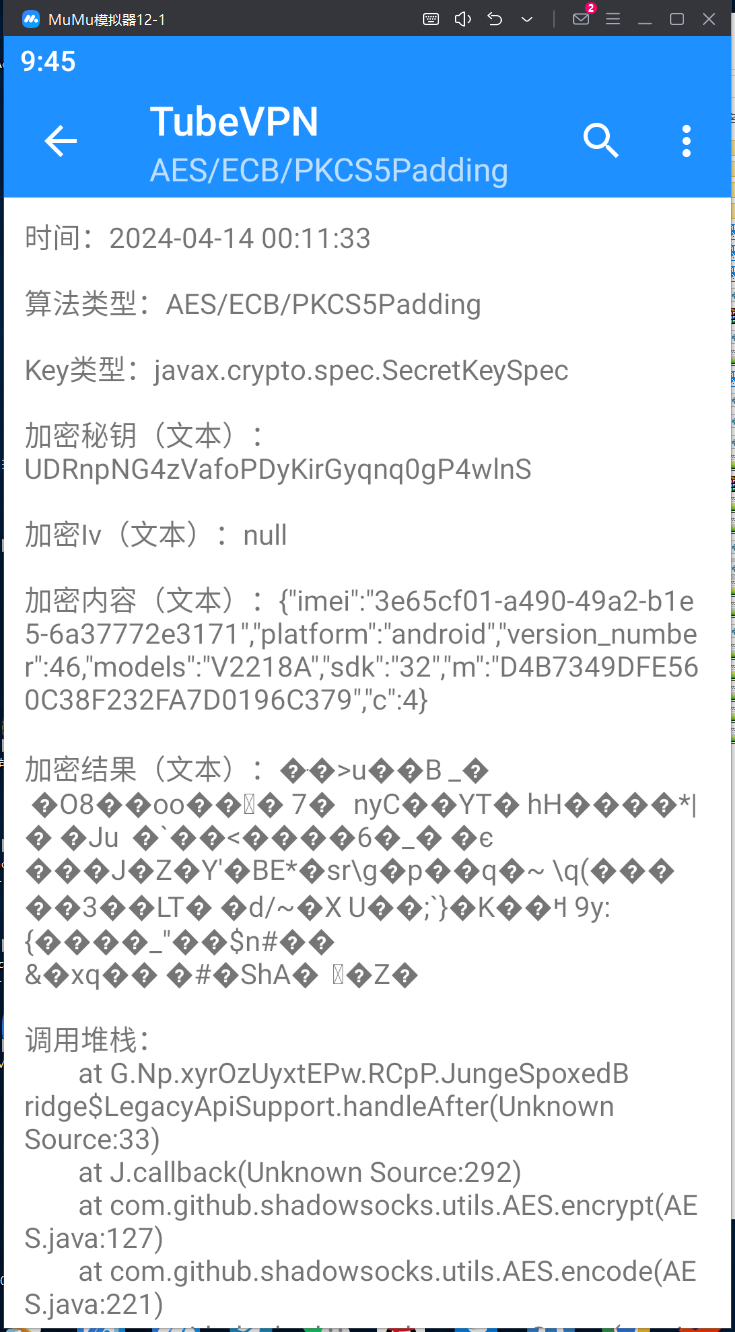
这里直接记录下加密密钥KEY
UDRnpNG4zVafoPDyKirGyqnq0gP4wlnS
然后使用网页在线工具测试一下刚抓包得数据是否对应得上
https://tool.lmeee.com/jiami/aes
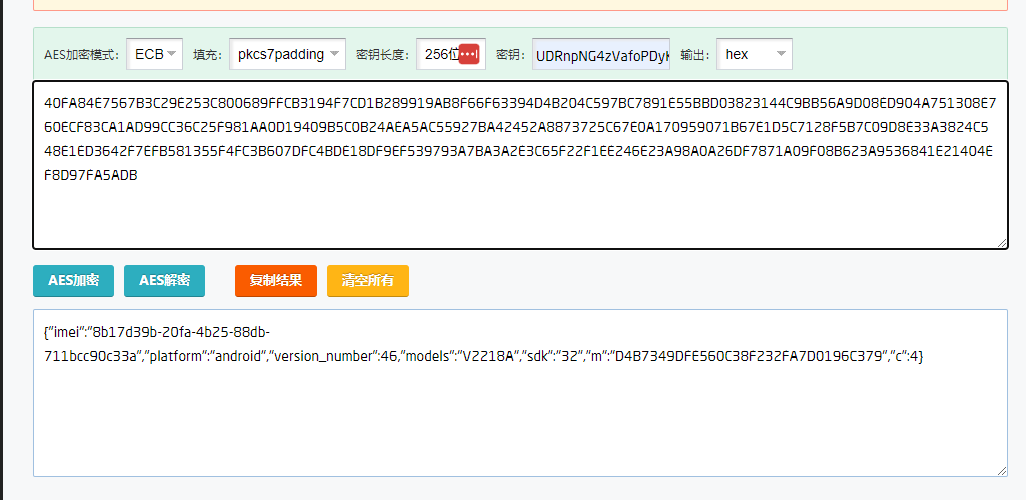
整个流程清楚了。就是通过这个请求,然后获取一天免费使用时间,破解清空缓存得原理就是随机一下IMEI这个值就行
如果是直接提取节点得话,就只能够用一天。一天后就会失效。然后我想了下。让程序直接每次都获取一次一天有效得节点
- # -*- coding: utf-8 -*-
- #隐士博客(kjol.cc)
- from ssl import VERIFY_DEFAULT
- from Crypto.Cipher import AES
- from Crypto.Util.Padding import pad, unpad
- import binascii
- import uuid
- import requests
- from datetime import datetime
- import json
- import base64
- from flask import Flask, request, jsonify
- app = Flask(__name__)
-
- @app.route('/generate-ssr-link', methods=['POST'])
- def generate_uuid():
- return str(uuid.uuid4())
- def aes_encrypt(plaintext, key):
- cipher = AES.new(key, AES.MODE_ECB)
- padded_text = pad(plaintext, AES.block_size)
- encrypted_bytes = cipher.encrypt(padded_text)
- return binascii.hexlify(encrypted_bytes).decode('utf-8').upper()
-
- def aes_decrypt(encrypted_hex, key):
- encrypted_bytes = binascii.unhexlify(encrypted_hex)
- cipher = AES.new(key, AES.MODE_ECB)
- pt = unpad(cipher.decrypt(encrypted_bytes), AES.block_size)
- return pt
- def send_post_request(url, data):
- current_time = datetime.now().strftime("%Y年%m月%d日 %H:%M:%S")
- data['t'] = f"t={current_time}"
- response = requests.post(url, data=data,verify=False)
- return response
-
- url = "https://edgeapi.mmasafe.com/node/getInformation_ex"
- key = b'UDRnpNG4zVafoPDyKirGyqnq0gP4wlnS'
-
-
- @app.route('/tube', methods=['GET'])
- def tube():
- server_index = int(request.args.get('id', default=0))
- new_uuid = generate_uuid()
- plaintext = b'{"imei":"3e65cf01-a490-49a2-b1e5-6a37772e3171}","platform":"android","version_number":46,"models":"V2218A","sdk":"32","m":"D4B7349DFE560C38F232FA7D0196C379","c":4}'
- plaintext = plaintext.decode('utf-8').replace('3e65cf01-a490-49a2-b1e5-6a37772e3171', new_uuid).encode('utf-8')
- encrypted_hex = aes_encrypt(plaintext, key)
- data = {
- "value": encrypted_hex
- }
- response = send_post_request(url, data)
- encrypted_hex = response.json().get('data')
- # 解密
- decrypted_text = aes_decrypt(encrypted_hex, key)
- json_string = decrypted_text.decode('utf-8')
- response_data = json.loads(json_string)
- encoded_link = ''
- if server_index <= 0 or server_index >= len(response_data['goserverlist']):
- for server in response_data['goserverlist']:
- city = server['name']
- password = server['password']
- server_ip = server['host']
- server_port = server['remotePort']
- method = server['method']
- city_encoded = base64.b64encode(city.encode('utf-8')).decode('utf-8')
- password_encoded = base64.b64encode(password.encode('utf-8')).decode('utf-8')
- protoparam_encoded = base64.b64encode(server['protocol_param'].encode('utf-8')).decode('utf-8')
- ssr_link = f"{server_ip}:{server_port}:{server['protocol']}:{method}:{server['obfs']}:{password_encoded}/?remarks={city_encoded}&protoparam={protoparam_encoded}&obfsparam="
- encoded_link = encoded_link + "ssr://" + base64.b64encode(ssr_link.encode('utf-8')).decode('utf-8')+'\n'
- return encoded_link
- server = response_data['goserverlist'][server_index]
- city = server['name']
- password = server['password']
- server_ip = server['host']
- server_port = server['remotePort']
- method = server['method']
- city_encoded = base64.b64encode(city.encode('utf-8')).decode('utf-8')
- password_encoded = base64.b64encode(password.encode('utf-8')).decode('utf-8')
- protoparam_encoded = base64.b64encode(server['protocol_param'].encode('utf-8')).decode('utf-8')
- ssr_link = f"{server_ip}:{server_port}:{server['protocol']}:{method}:{server['obfs']}:{password_encoded}/?remarks={city_encoded}&protoparam={protoparam_encoded}&obfsparam="
- encoded_link = encoded_link + "ssr://" + base64.b64encode(ssr_link.encode('utf-8')).decode('utf-8')
- return encoded_link
-
- if __name__ == '__main__':
- app.run(host='0.0.0.0',port=80,debug=True)
如果只想使用某条指定得线路,传入ID参数
如我只想使用第一条线路
http://py.kjol.cc/tube?id=1
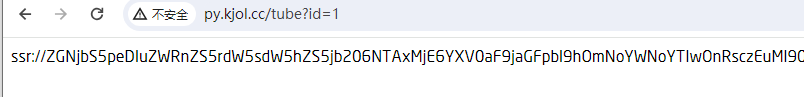
返回得是一条单独得SSR链接。然后找个在线订阅转换
我尝试了一下使用https://id9.cc/转换
在线订阅转换地址有如下
https://acl4ssr-sub.github.io/
https://sub.dler.io/
https://sub.pet/
https://bianyuan.xyz/
https://sub.pet/
https://sublink.dev/
https://sub.tsutsu.one/
https://nexconvert.com/
https://api.nameless13.com/
https://sub.ssltd.xyz/
https://sub.tronet.cloud/
个人喜欢https://acl4ssr-sub.github.io/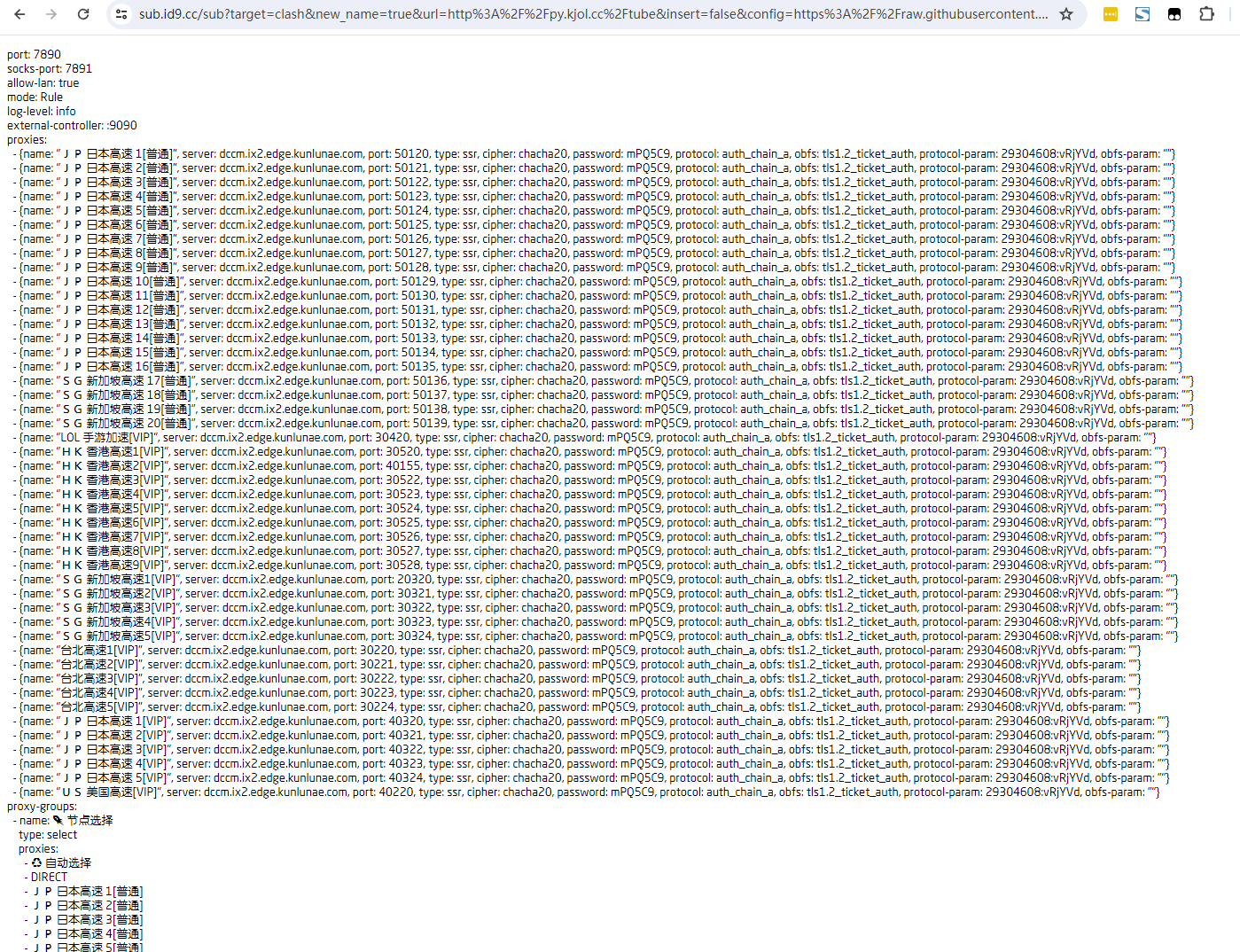
配上定时24小时内自动更新订阅,或者失效就手动更新订阅
后续是不是加什么混淆参数了呀,服务器不通了
添加协议头,还有频繁请求会把你IP拉黑了,上节点池,缓存请求数据,减少请求次数
问一下,这个协议头还能怎么加勒?节点池到好理解
ip被拉黑是永久的还是暂时的
已经修复,可以使用了得
有问题了现在